The Ultimate Guide to GDPR Data Breach Responses
If you think that data breaches only happen to someone else, think again. Data breaches have happened to all types of businesses - from small ecommerce stores to large corporations such as Microsoft and it could happen to you as well. Read about GDPR Data Breach Responses here.
If you think that data breaches only happen to someone else, think again. Data breaches have happened to all types of businesses - from small ecommerce stores to large corporations such as Microsoft and it could happen to you as well.
Each time your company suffers a breach, it's like opening your door to someone from the outside - they've gained access to your confidential information and can use it to their advantage. But this isn't the only type of security breach that affects your company. Every time someone tries to break into your building, or your computer systems are compromised by malware or viruses, that's a data breach too. In fact, data breaches are the only types of security breaches that affect personal data.
Data breaches and abuse cost businesses a lot of money - both financially and in terms of their reputation. Fines for data breaches can be huge, while abuse of customer data can lead to a loss of customers, reduced sales, and even loss of business altogether. Not only do these incidents damage your bottom line, they also cause a lot of stress and pain for your employees.
According to IBM’s Data Breach Report 2021, the data breach costs for businesses keep increasing steadily, rising 10% annually on average. Businesses have been losing 38% of their market share on average due to data breaches.
Is a 38% drop too much for your business? If it is, you need to implement breach prevention measures and have a data breach response plan in place. When a breach occurs, you need to respond to it as required by the law and reduce the damage.
What is a Data Breach
A data breach means the loss of, unauthorized access to, or unauthorized disclosure of personal information resulting from a security breach.
It could appear as:
- Data Destruction
- Damage of data
- Loss of control over data
- Unauthorized access or disclosure of data, or other.
Data protection laws require businesses to protect personal data from unauthorized access. When an unauthorized person accesses the data, you have a data breach.
It doesn’t matter whether the unauthorized person is an evil hacker who wants to steal and abuse your data or your employee or contractor who should not have access to the data - as long as the access is unauthorized, it is a data breach.
It also doesn’t matter whether personal data has been abused or not. A breach is still a breach.
Finally, it doesn’t matter whether the unauthorized person has no effective access to the personal data or if their access poses a threat to the rights and freedoms of your data subjects. The breach happens at the moment of unauthorized access.
Data breach vs. data security breach
A data breach as defined in the GDPR is different from a data security breach.
A security breach means a breach of your information system. Sometimes these breaches do not involve unauthorized access to personal data, therefore they are not personal data breaches.
However, all data breaches occur due to some data security failures. Therefore all data breaches are security breaches.

It's no secret that data breaches happen every day. Unfortunately, this is due to data security failures on the part of the organization that was breached. In order to prevent future data breaches, it's important to understand the difference between a data security breach and a data security incident. A data security breach is when unauthorized access is gained to protected data. A data security incident, on the other hand, is when protected data is accessed but does not meet the definition of a breach.
Types of data breaches
There are many criteria to divide personal data breaches into types.
Personal data breaches can be classified according to what caused them. This is done by looking at internal factors, such as misuse of your own employees, or externally caused factors, such as a cyber attack. These are the most common breaches that occur regularly:
- Ransomware - when a malicious code encrypts personal data and then demands a ransom from the controller in exchange for the decryption code.
- Data exfiltration (or data leakage) - when the data is copied, transferred or retrieved from your servers by an unauthorized person (it can be your employee or someone from outside your organization.
- Internal human errors by your employees. Whether intentional or unintentional, they lead to a data breach.
- When devices and paper documents stolen from you contain personal data.
- Mispostal - when an unauthorized employee gains access to personal data sent by mail or email as a result of human error.
- Social engineering - the psychological manipulation of people into performing actions involving the disclosure of personal data. The most common form includes identity theft and email exfiltration (phishing attack)
What to do in case of a data breach
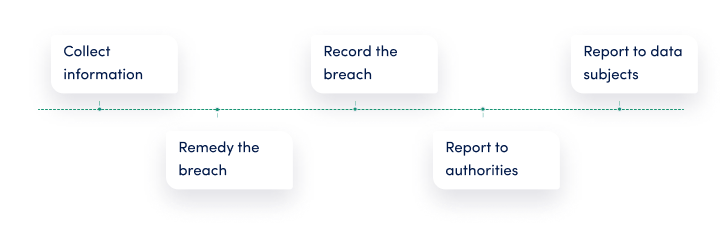
When a data breach occurs, you need to do some or all of the following actions:
- Collect as much information as possible about the breach. You’ll need this information to report to the authorities and data subject and will help you remedy the breach, if possible.
- Remedy the breach. The first thing to do upon discovering the breach is to do your best to remove the negative consequences of the breach. It won’t always be possible to remove them, but if there is something that you could do, consider doing it.
For example, in the case of a mispostal, you can reach out to the receiving person to ask them to delete the personal data they have received.
On the other hand, in the case of a big data leak of encrypted data, there is not much you can do.
- Record the breach. You must maintain breach records of all the breaches that have occurred to you. The records should contain information such as the time and date of the breach, the nature of the breach, what happened, what has been done to remedy the breach, any reports to authorities and data subjects, and other information.
Sometimes you’ll need to report the breach to authorities and data subjects, but in some cases, it won’t be necessary. Recording the breach is the only action you must take in all data breaches.
- Report to DPA. Most data breaches have to be reported to the relevant data protection agency. There are very few breaches, such as mispostal or theft of encrypted data, where all you need to do is record the breach.
When to report
GDPR requires data controllers to report the breaches to the data protection agency within 72 hours of discovering the breach. You can report later than those 72 hours only if you have a good reason. However, reporting later without a sufficient reason leads to penalties.
How to report
You can report in any way you find suitable. In fact, some agencies have breach reporting forms on their websites, but they are not obligatory. When you become aware of a personal data breach, what is important is to report the breach. It doesn’t matter how you do so.
Simply put, you can just pick up the phone and call the agency. You can use the breach reporting form on their website, if any. You can send them an email. It really doesn’t make a difference. You’ll be compliant as long as you report it within 72 hours of becoming aware of the breach (or later if you have a good reason for that).
What information to include in the report
You need to include at least the following:
- The nature of the personal data breach
- The categories of data breached, where possible
- The number of persons affected, where possible
- The name and contact details of the Data Protection Officer or another contact person
- The likely consequences of the breach
- The measures taken to mitigate the adverse effects
You can add any other information that you find relevant. No two breaches are the same, therefore no two breach reports are the same.
How does the reporting procedure look like
You report the breach. Someone from the agency guides you on what you need to do next and you cooperate. That’s the only predictable step. The rest depends on the nature of the breach.
- Report to data subjects. Some data breaches have to be reported to data subjects whose personal data has been exposed to unauthorized access. You must inform the data subject about the breach when it poses a risk to their rights and freedoms.
For example, when their health history data or dating app behavior has been exposed or their private communication related to work. The report shall contain the same information reported to the data protection authority.
How to Prevent Personal Data Breaches
There are measures that will significantly reduce the chances of having a data breach. However, there are some things to note:
- Cyber attackers continuously seek new ways to get around security measures
- That is why this is not a set-it-and-forget-it. You need to review and update your measures accordingly all the time.
Your measures depend on your business circumstances, the amount of data you process, the sensitivity of the data, and so on. See our post on how to track your website visitors without breaking the law.
Some of the measures you could implement include:
- Periodic implementation of training, education, and awareness programs for employees on their privacy and security obligations
- Keeping all software up-to-date
- Design processes or isolate data systems and networks to avoid malware attacks
- Have an up-to-date, secure, and tested backup procedure in place
- Install an up-to-date anti-malware software and firewall
- Strong encryption and authentication, particularly for admin roles
- State-of-the-art encryption
- Use of strong authentication methods like two-factor authentication and authentication servers, complemented by an up-to-date password policy
- Secure development standards include the filtering of user input (as much as possible, use whitelisting)
- Strong user privileges and access control management policy
- Use of appropriate, up-to-date, effective, and integrated firewall, intrusion detection, and other perimeter defense systems
- Conduct of regular systematic IT security audits and vulnerability assessments (penetration testing)
- Device encryption
- Password/passcode device protection
- Use VPN to connect mobile devices to data back-end servers
- Proper regulation of device usage inside and outside the company
- Avoid storing sensitive information in mobile devices or hard drives
Have a data breach response plan
There's no way to sugarcoat it: data breaches happen to everyone. Your business is not immune and you better be prepared if and when it happens. This is why having a data breach response plan in place will make things easier and simpler for you. When a breach occurs, you'll know exactly what to do to minimize the negative effects of the breach.
No two businesses are the same, therefore no two data breach response plans are exactly the same but there are common elements that make them good.
A comprehensive plan may be made of the following parts:
- Risks overview. You need to become aware of your risks and write them down in a document. This overview will inform your next steps, such as what kind of response team you need, what tools for remedy to use, how to communicate the breach, and so on.
- Data breach response team outline. Depending on the nature of the risks, you need to outline the team that will be responsible to handle the breach once it occurs.
- Internal notification procedures. Your employees or contractors will discover your data breaches. They need to know exactly what to do in such a situation. You have to create an internal notification procedure they could follow to ensure that the breaches are reported properly, that the breach could be remedied, and that negative consequences will be mitigated.
- Remedy procedures. Once a breach is reported to your data breach response team, it is time to attempt to remedy the breach. If it is possible, this would vastly reduce the possible penalties and maybe save your reputation. This is why your response team needs to have clear remedy procedures in place.
- Procedures for notifications of authorities and data subjects. Unlike the other elements of the plan, your procedures for notifying authorities and data subjects are constrained by the notification legal requirements. Having these constraints in mind, lay down procedures of who should do what to make the reports within the 72-hour timeframe to avoid further penalties for reporting late.
- A communications plan. You’ll have to communicate the breach with the public and you’ll have to do it quickly and effectively. That is where a flexible draft communication strategy will come in handy. It is wise to have press release drafts ready to be adjusted to the current situation and sent to the media.
Of course, this is not an exhaustive list. Let it guide you, but make sure you adjust your plan to your specific circumstances.
Final Thoughts
A data breach is a disaster waiting to happen to any business that doesn’t take care of data security. It may happen to you as well. In fact, your employees may be breaching personal data on a regular basis if you have no data protection policies in place and they have unauthorized access to clients’ personal data.
Data breaches are one of the leading reasons for GDPR penalties, so you have to do what you can to secure your data and avoid them.
Find the best Secure Privacy plan for your organization and sign up here for a free trial.

ISO 42001 Implementation: A Practical Guide to Building an AI Management System (AIMS)
Your organization deploys AI for credit scoring, customer service automation, and predictive analytics. Your data science team builds models. Your security team secures infrastructure. Your legal team reviews contracts. And yet, when a regulator asks "how do you govern AI risk across its lifecycle?" or "demonstrate your controls for algorithmic bias," no single team owns the answer — because AI governance exists in fragments, not as an integrated management system.

NIST Privacy Framework: The Complete Enterprise Guide to Privacy Risk Management
Your organization collects customer data across web, mobile, and IoT platforms. Your cybersecurity team secures that data against external threats. Your legal team drafts privacy policies. And yet, when a hospital employee with authorized system access shares a celebrity patient's records with media, or when a properly secured billing system merges two patients' data due to a configuration error, no existing control prevented the privacy harm—because the risk came from authorized data processing, not a security breach.

California DROP Act (CPRA) 2026: Compliance Requirements and DSAR Automation
California just made consumer privacy deletion requests unavoidable at scale. Starting August 1, 2026, every registered data broker must connect to a state-operated platform, retrieve consumer deletion requests every 45 days, and process them—automatically, verifiably, and repeatedly. Miss a deadline and face $200 per-request daily penalties. Fail to propagate deletions to vendors and face enforcement scrutiny that has already produced settlements exceeding $1.5 million.
- Data Protection
- Privacy Governance
