Navigating GDPR Compliance: Essential Steps for GDPR Data Mapping for Privacy Compliance
Discover vital steps for GDPR data mapping, enhancing transparency and mitigating risks. Learn about challenges, best practices, and how Secure Privacy simplifies the process. Ensure robust data protection effortlessly.
As data protection regulations continue to evolve and privacy concerns gain prominence, organizations must ensure compliance with the General Data Protection Regulation (GDPR). One crucial aspect of this privacy law compliance is data mapping, which involves understanding and documenting how personal data flows within an organization. Effective data mapping lays the foundation for privacy compliance by providing insights into data processing activities, identifying potential risks, and facilitating the implementation of necessary safeguards.
In this article, we will explore the essential steps for GDPR data mapping, equipping organizations with a solid framework to navigate the complexities of privacy compliance and safeguard personal data in accordance with GDPR requirements.
What is data mapping for GDPR?
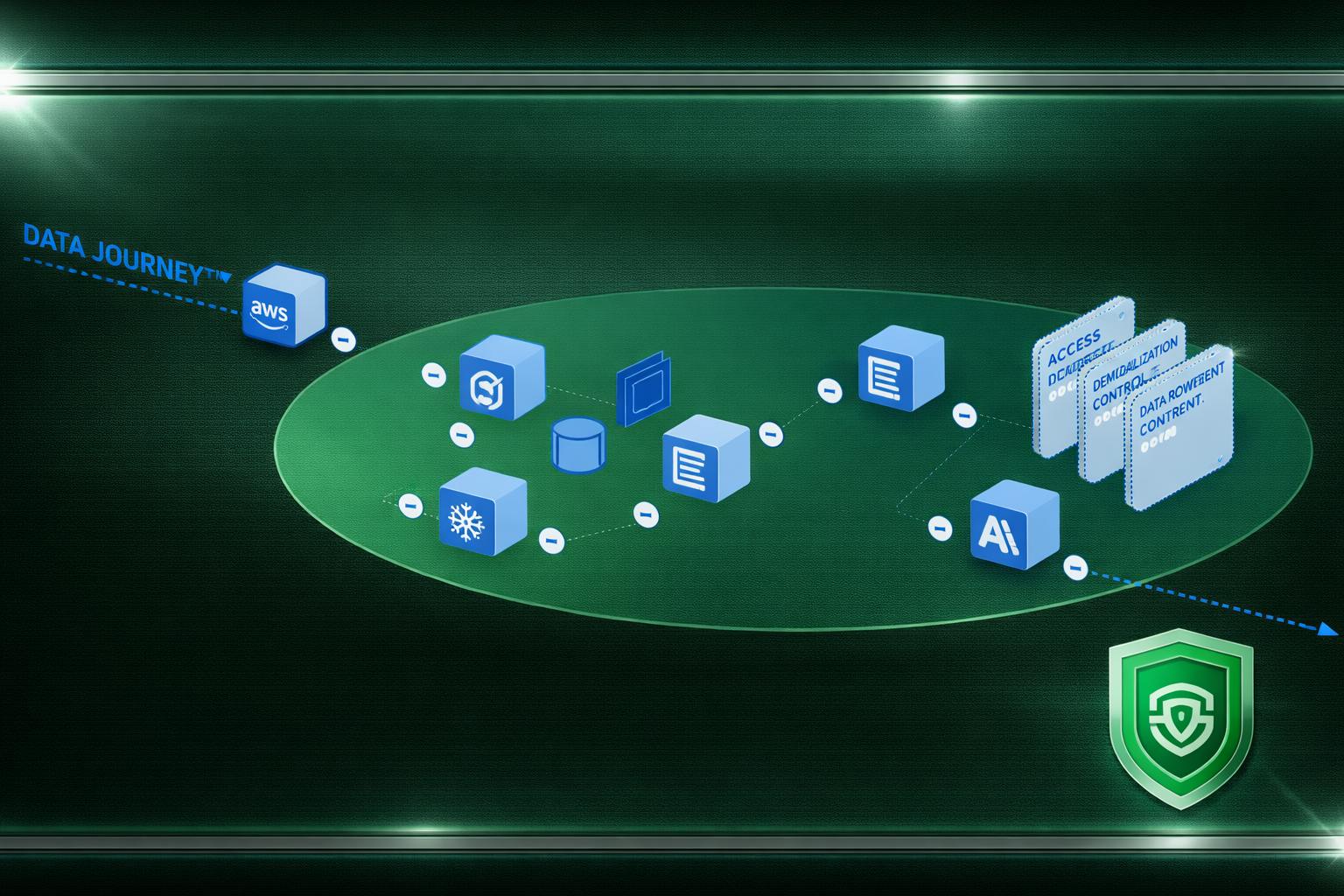
Data mapping, also known as data flow mapping, is the process of visually outlining the journey of personal data within an organization. This comprehensive process involves identifying, categorizing, and documenting every step that personal data takes, from the point of collection to its eventual deletion or disposal.
Think of it like creating a detailed roadmap for your personal data, showing where it originates, where it travels, and what happens to it along the way. This map helps organizations understand:
- What personal data they hold: This includes names, addresses, email addresses, IP addresses, financial information, and any other data that can be used to identify an individual.
- Why they process the data: Organizations must have a legitimate reason for collecting and processing personal data, such as fulfilling contracts, complying with legal obligations, or pursuing legitimate interests.
- Where the data is stored: This includes both physical locations, like servers, and digital locations, like cloud storage.
- Who has access to the data: This includes employees, third-party vendors, and any other authorized individuals or entities.
- How long the data is kept: Organizations should only retain personal data for as long as necessary for the purposes for which it was collected
The term “data mapping” is not mentioned in the GDPR, so some argue it’s not truly mandatory. However, the GDPR does require businesses to meet requirements like creating records of processing activities (RoPA), fulfilling data subject access requests (DSAR), and conducting data protection impact assessments (DPIA). Without data mapping, complying with these requirements is not possible.
What is a data flow?
A data flow, in simple terms, is the path that personal data takes as it moves through an organization's systems and processes. It's a visual representation of how data travels, detailing its journey from collection to use, storage, transfer, and eventual deletion or anonymization.
Why is data mapping important for GDPR compliance?
Data mapping is hugely important for GDPR compliance due to its ability to address several key requirements and deliver significant benefits. Data mapping can be an important part of GDPR compliance with Articles 30 and 36. Article 30 requires documentation of certain organizations processing. Article 36 requires organizations to conduct Data Protection Impact Assessments before engaging in certain processing.
Here's why data mapping is essential:
- Transparency and Accountability:
- Understanding your data: Mapping exposes the entire journey of personal data, revealing what's collected,how it's used, and where it's stored. This transparency is crucial for meeting GDPR's principle of accountability. - - Demonstrating compliance: A well-maintained data map serves as tangible evidence of your efforts to comply with GDPR. It's a valuable tool when responding to regulatory inquiries or defending against potential complaints.
- Risk Mitigation and Data Protection:
- Identifying vulnerabilities: Data mapping exposes areas where personal data might be at risk, allowing you to focus security efforts on critical points. You can pinpoint potential weak spots in storage, transfer, or access points. - - Implementing safeguards: With a clear understanding of data flows, you can tailor security measures specifically to address identified risks. This could involve encryption, access controls, or data minimization strategies.
- Fulfilling Data Subject Rights:
- Responding to access requests: Knowing exactly where data is stored and used makes it easier and faster to respond to data subject access requests. You can efficiently locate and extract relevant information to fulfill these obligations. - - Facilitating the right to be forgotten: Data mapping helps you track down and erase personal data upon request, ensuring you comply with the "right to be forgotten" provision.
- Improved Efficiency and Business Benefits:
- Streamlining data processes: Mapping your data flows can reveal inefficiencies and redundancies in data handling. This can lead to process improvements, saving time and resources. - - Informed decision-making: Having a holistic view of your data empowers you to make informed decisions about data collection, storage, and usage. This can translate to better customer experiences, enhanced security postures, and cost optimization.
Overall, data mapping serves as a fundamental tool for navigating the complexities of GDPR compliance. It promotes transparency, mitigates risks, empowers data subjects, and optimizes data management, ultimately contributing to a stronger data privacy culture within your organization.
What are the key steps involved in GDPR data mapping?
GDPR data mapping involves several key steps to comprehensively understand and document the flow of personal data within an organization. These steps include:
- Identifying Personal Data: Begin by identifying the types of personal data your organization collects and processes. This could include information such as names, addresses, email addresses, financial details, or any other data that can directly or indirectly identify an individual.
- Mapping Data Flows: Document how personal data moves within your organization. Identify the sources of data, such as data collection forms or systems, and trace its path as it is stored, processed, and potentially shared with third parties. This step provides a visual representation of how data flows throughout your organization's systems and processes.
- Assessing Data Processing Activities: Evaluate the purposes for which personal data is collected and processed within your organization. Determine the legal bases for processing, such as consent, contractual necessity, or legitimate interests, and document them accordingly. Additionally, assess if any personal data is transferred to countries outside the EU/EEA and ensure appropriate safeguards are in place.
- Conducting a Data Inventory: Create a comprehensive inventory of the personal data your organization holds. This inventory should include details such as the categories of personal data, the purposes of processing, the retention periods, and the lawful bases for processing. This step helps in understanding the scope and nature of personal data processing activities.
- Reviewing Data Protection Measures: Assess the security measures and policies in place to protect personal data. This includes evaluating technical and organizational measures to ensure the confidentiality, integrity, and availability of the data. Identify any gaps or vulnerabilities and implement appropriate safeguards and controls to mitigate privacy risks.
- Updating Privacy Documentation: Document the findings of your data mapping exercise in privacy notices, data protection impact assessments (DPIAs), and other relevant privacy documentation. These documents should reflect accurate and up-to-date information about the personal data your organization processes and the associated data protection practices.
For many companies, this process is simple, sending quarterly surveys or assessments and then manually integrating updates into the existing data map. Due to the complexity and time required, automated data mapping using data mapping software is often a better choice.
For more information, check out this free GDPR data mapping checklist.
What are the data mapping best practices?
Conquering GDPR compliance requires a clear understanding of your data's journey. Enter data mapping, your roadmap to data privacy success. Here are some key best practices to make the most of it:
- Identify all data sources: Don't miss a single nook and cranny! Websites, forms, apps, even employee records – every point of data collection needs to be mapped.
- Trace the data's entire lifecycle: From collection to storage, usage, transfer, and deletion, map every step. Think of it like following a river's journey from source to sea.
- Capture details at every stage: Legal bases, retention periods, security measures, data subject rights – leave no stone unturned in your documentation.
- Identify risks and compliance gaps: Be your own data detective! Look for areas where you can minimize data, improve security, or clarify consent mechanisms.
- Implement improvements: Don't just map, act! Update processes, deploy new technologies, and revisit data retention policies based on your analysis.
- Regularly review and update your map: Data and regulations evolve, so your map should too. Think of it as a living document, constantly adapting to your data landscape.
Businesses can leverage automation tools and data visualization techniques to make mapping easier and more efficient.
What are the key challenges of data mapping?
Data mapping poses several challenges that organizations may face:
- Complexity and Fragmentation: Organizations often have complex data ecosystems with disparate systems and databases. Identifying and mapping the types of data flows across these interconnected systems can be challenging, especially when data is fragmented across different departments or business units. Lack of centralized data management and documentation further complicates the process, making it difficult to obtain a holistic view of personal data processing activities.
- Third-Party Involvement: Many organizations rely on third-party vendors, partners, or service providers who may process personal data on their behalf. Mapping data flows that involve these external entities can be complex, as organizations may have limited visibility and control over how these parties handle the data. Ensuring compliance and understanding the implications of data sharing with third parties adds an additional layer of complexity to the data mapping process.
- Evolving Data Ecosystems and Technical Limitations: Organizations undergo continuous changes, introducing new systems, applications, or data processing activities. Keeping data mapping up to date and incorporating changes in the data ecosystem can be challenging, especially when dealing with legacy systems or incompatible data formats. Technical limitations can hinder the accurate tracing of data flows and understanding the relationships between different data elements, making data mapping more complex and time-consuming.
Addressing these challenges requires a proactive approach, including establishing robust data governance practices, promoting collaboration among stakeholders, and leveraging technology solutions that facilitate data mapping and documentation.
What are the benefits of going beyond the minimum requirements for GDPR compliance?
Going beyond the minimum requirements for GDPR compliance offers several benefits. It demonstrates a commitment to data protection and privacy, enhancing trust with customers and stakeholders. Additionally, it provides a competitive advantage by differentiating organizations in the marketplace. Furthermore, going beyond the minimum requirements helps mitigate risks and strengthen overall data protection practices.
How often should I update my GDPR data map?
The frequency of updating your GDPR data map depends on various factors, including the size of your organization, the complexity of your data ecosystem, and the rate of change in your data processing activities. As a general guideline, it is recommended to review and update your data map at least annually or whenever significant changes occur that may impact data flows or data processing activities.
Ensuring compliance requires your company's data map must be up-to-date, encompassing all relevant tools, databases, and systems. Therefore, implementing a process that guarantees continual updates is of utmost importance.
I'm a small business. Do I still need to worry about GDPR data mapping?
Yes, even as a small business, it is important to consider GDPR data mapping. The General Data Protection Regulation (GDPR) applies to organizations of all sizes if they process personal data of individuals within the European Union (EU), regardless of where the business is located. Data mapping is a fundamental aspect of GDPR compliance, as it helps you understand how personal data flows within your organization and enables you to assess and manage associated risks.
While the scale and complexity of data mapping may vary depending on the size of your business, taking a proactive approach to data mapping can help you demonstrate compliance with GDPR requirements, build trust with your customers, and enhance your data protection practices.
How Secure Privacy can help as a data mapping tool for GDPR
Secure Privacy can be a powerful ally in tackling the complexities of GDPR data mapping. With their comprehensive compliance framework and documentation capabilities, Secure Privacy provides the necessary support to streamline your data mapping efforts. Take advantage of Secure Privacy's expertise and tools to simplify your GDPR data mapping process and ensure robust data protection.
Schedule a call with Secure Privacy today to learn more and start mapping your data securely.
Get Started For Free with the
#1 Cookie Consent Platform.
No credit card required
Consent Management for AI Training Data: How to Control LLM Crawlers and Enforce Opt-Out at Scale
Your organisation published a detailed research report six months ago. Last week, a competitor’s AI-powered tool started surfacing insights that mirror your proprietary methodology almost word for word. You did not license your content. You did not consent to its use. And you have no audit trail proving you ever tried to stop it.
- AI Governance
- Data Protection

What Is GDPR? A Practical Guide for Businesses
GDPR isn't a compliance checklist: it's an operating system for how your organization discovers, uses, protects, and proves control over EU personal data. Most businesses treat GDPR as a one-time legal project, building policies and spreadsheets that become outdated within months. That approach fails the moment regulators request current documentation, customers demand evidence of compliance, or your business scales beyond manual processes.
- Legal & News
- Data Protection

What Is Privacy Governance? A Practical Guide for Businesses
Privacy compliance checks a box. Privacy governance builds a system. Most organizations treat privacy as a legal requirement—scrambling to answer auditor questions, patching policies after incidents, and hoping their spreadsheets hold up under regulatory scrutiny. That approach fails the moment your business scales, enters new markets, or adopts technologies that transform how data flows.
- Privacy Governance

